Why Choose Kriptor?
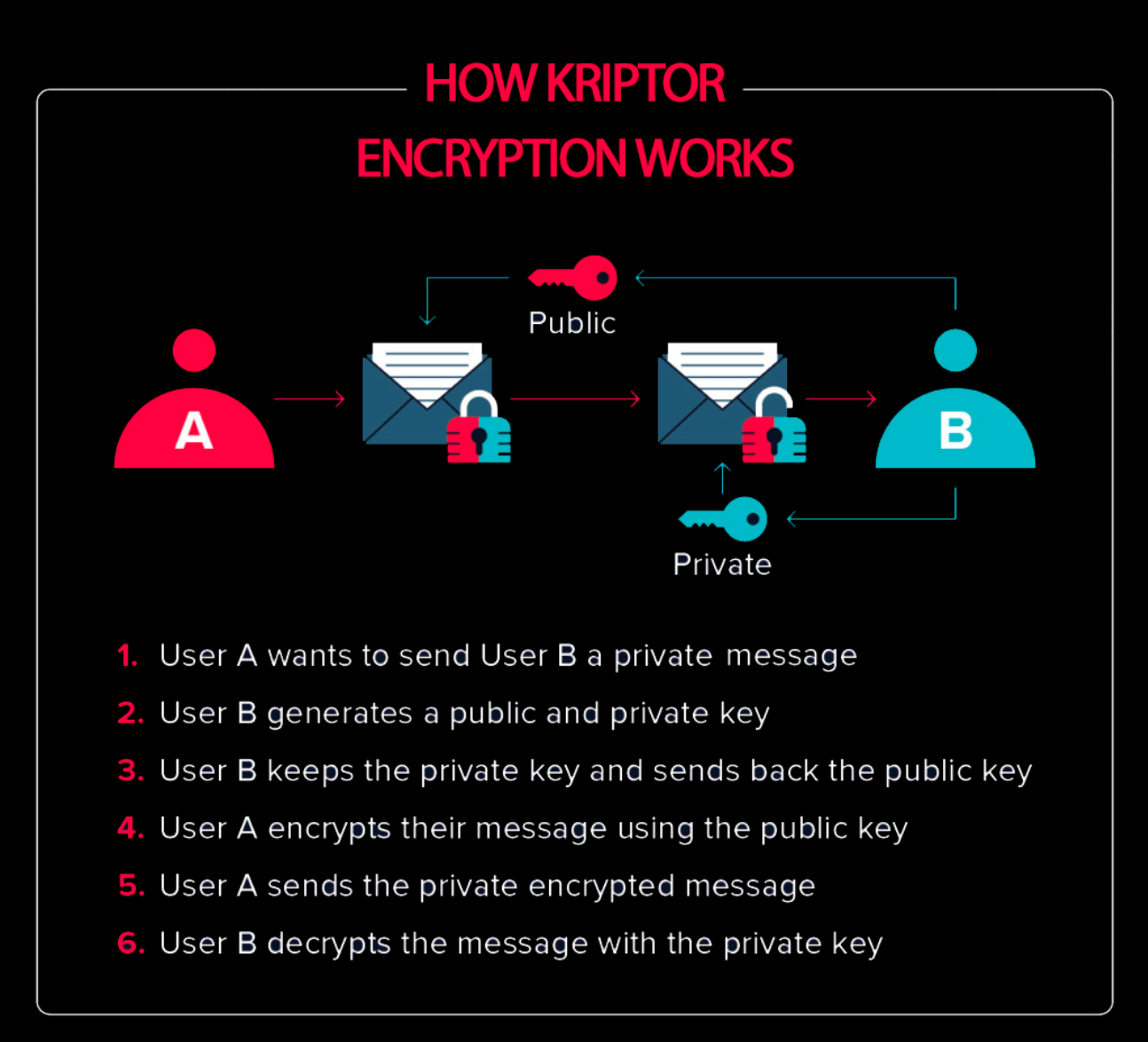
Kriptor is a unique messaging application designed for maximum privacy. Unlike traditional messaging apps, it operates entirely without internet, servers, or cloud storage, relying exclusively on encrypted SMS for transmission. This ensures that your messages remain private and accessible only on your device.
Request Kriptor via EmailWho Should Use Kriptor?
Kriptor is perfect for:
- Governments
- Enterprise CEOs and Executives
- Journalists
- Security-sensitive individuals
Messaging App Comparison
| Feature |  Kriptor Kriptor |
 Signal Signal |
 WhatsApp WhatsApp |
 Telegram Telegram |
|---|---|---|---|---|
| End-to-End Encryption | Yes, RSA 2048-bit (no servers) | Yes (Signal Protocol) | Yes (Signal Protocol) | Secret chats only |
| Private Key Management | Stored only on device | App managed | App managed | App managed |
| Messages after device change | Unreadable | Yes | Yes | Yes |
| Server/Cloud Usage | No | Yes | Yes | Yes |
| Internet Dependency | No, uses SMS | Yes | Yes | Yes |
| Interception Risk | Impossible without device | Low | Moderate (cloud backup) | High (non-secret chats) |
| Public Availability | Email request only | Public | Public | Public |
| Private Key Reset (Making messages unreadable in case of compromised device) | Yes | No | No | No |
| Metadata Leaked | None (no internet activity) | Phone number, timestamps | Phone number, timestamps, contacts | Phone number, usernames, IP |
Technical Details: Hardware-based Keystore Security
Kriptor uses a hardware-based keystore to securely store your private key. This ensures the private key is generated and maintained within a protected hardware environment, inaccessible to the operating system or applications. Your private key is never exported or loaded into device memory, making it completely secure from external threats.
Protection Against Attacks:
- Resistant to Cold Boot Attacks
- Resistant to Memory Attacks
- Resistant to Dump Attacks
- Resistant to Root Attacks
Potential Vulnerabilities (Very Rare Cases):
- Device compromised at hardware level
- TEE compromised
- Biometric authentication bypassed
- Physical device tampering
The hardware keystore leverages secure cryptographic modules, like the Trusted Execution Environment (TEE) or Secure Element, ensuring cryptographic operations occur within a safe and isolated environment. This method enables strict access controls, such as mandatory user authentication for cryptographic operations, significantly enhancing security.
Due to these robust security measures, Kriptor is perfect for governments, enterprise executives, journalists, and other security-sensitive users who require unbreakable messaging privacy.
Request Access
Kriptor is free upon request. Please contact us via email:
Request Kriptor via Email